It’s Time to Go Beyond VPNs
Faction eliminates all cloud-based, centralized vulnerabilities and puts you in control of your security for networking, devices and data in a dangerous world
Deploy yourself or work with a Faction MSP partner
A Business VPN replacement for small to midsized organizations or collaborative teams that need to secure distributed workplaces with lots of smart, dumb and legacy devices. Deploy a Faction Virtual Private Circuit to get your critical devices OFF of the Internet and into your secure, private Faction Network.
360 Protection Controlled by You #
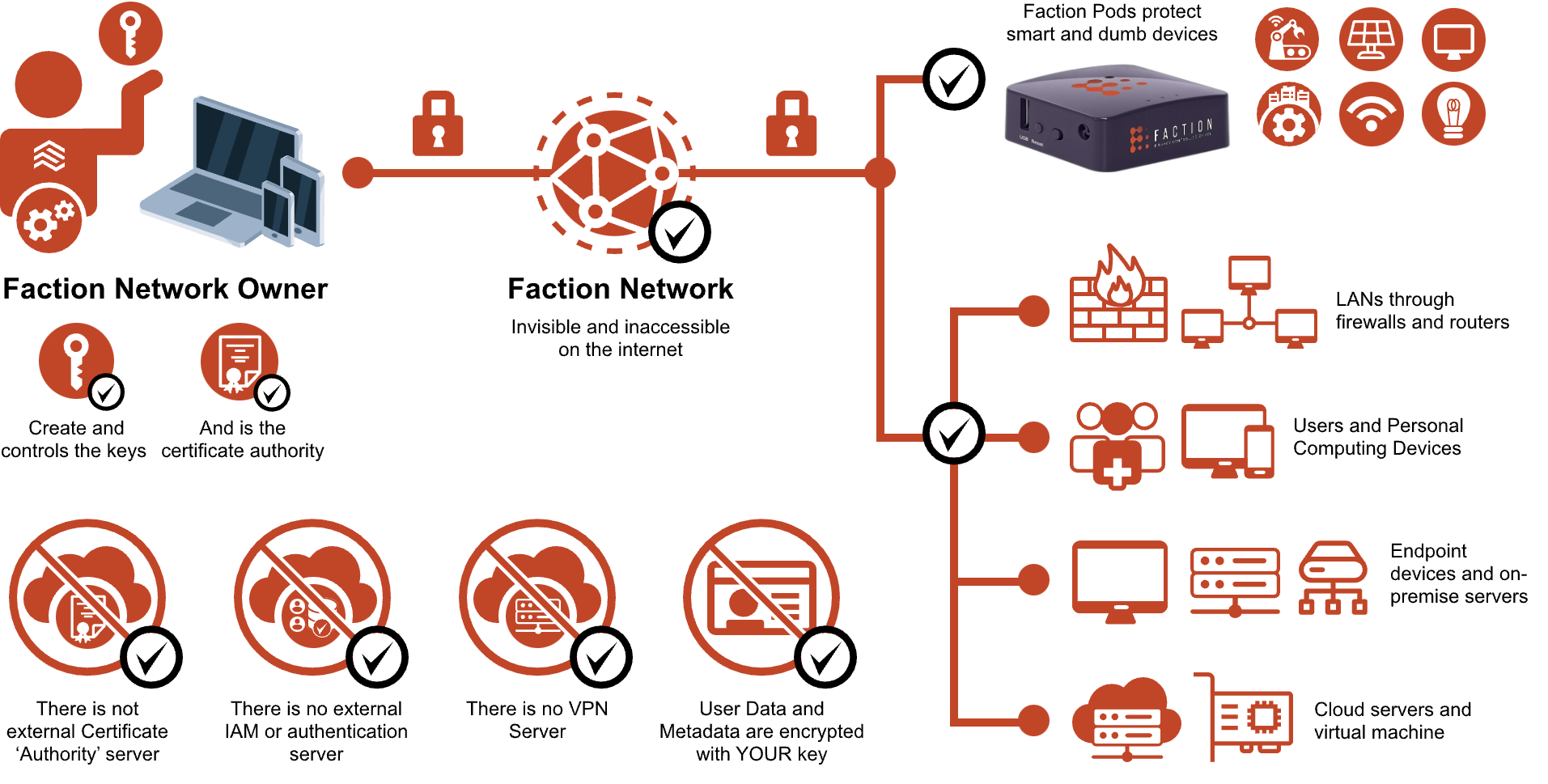
A Faction Virtual Private Circuit (VPC) is created and controlled only by your organization. It NOBODY – including Faction Communications – can see or access it unless invited and authenticate by you (or your administrator). It combines 3 layers of security together in one simple, easy to deploy and easy to use solution.
Faction Network #
Rapidly deploy secure private networks created, controlled accessible and visible only to you and your authorized users and devices
Faction Pods #
Take smart and dumb devices that connect protect themselves OFF of the Internet and into your private networks
Faction Data Encryption #
Encrypt data at all times – in transit and at rest – with keys created and controlled by the data owner
Remember the T1? We do. #
There was a day when no organization would have ever considered connecting mission critical devices – such as smart manufacturing machinery, home and personal healthcare devices, charging stations and other decentralized infrastructure – directly to the Internet. It is simply too risky.
For 30 years, organizations leased T-1 lines, a secure but costly way to have a totally private network to connect critical machines and devices and the computers and servers that are needed to monitor and control them. But then, something happened: T-1 lines were phased out! One by one, these internal networks were moved onto the Internet and securing these connections become the job of VPNs, Firewalls and SDNs.
Unfortunately, the Internet is fundamentally compromised and more organizations are discovering every day that these tools simply cannot secure mission critical machines and devices.
VPNs are not actually secure or private #
- Centralized Servers, With Human Access And Control
- Visible For Study And Attack
- Do Not Protect Data Except In Transit
SDNs are more secure and can micro-segment access but… #
- Still Have Centralized Control And Vulnerabilities
- Complex And Hard For End Users And IT
- Expensive Enterprise Solutions & Support
Neither can protect the critical smart and dumb devices that fill our workplaces, factories and lives #
Smart Office #
Cameras #
eHealthcare #
Smart Infrastructure #
Smart Manufacturing #
VPCs Are Simple, Low Cost and Totally Secure #
Faction VPCs are the perfect solution for small to midsized businesses to protect your critical networks, devices and data in a dangerous world.
- Eliminate the vulnerabilities of VPNs
- Avoid the complexity & cost of SDNs and ZTNA.
When you deploy a VPC, all of the computers, servers, devices – and any users that can see or access them – are put into private network created and controlled only by you. This radically reduces your attack surface and vulnerability to malicious external hacks of all kinds.
Virtual Private Circuits (VPCs) #
VPCs are for SMEs or collaborative teams of any size that need to secure distributed workplaces with lots of smart, dumb and legacy devices. Each customer can create and manage multiple Faction Networks, and generally will have custom deployment, configuration and integrations that include the wide scale use of Pods or Pods firmware.
- Any Organization with a Distributed Workplace. If like most organizations, your work environment spans staff, consultants and vendors across many locations (and travel) and includes the extensive use of BYOD, your are ripe for attack and need Faction!
- Manufacturers. Any company today that has a networked factory floor with smart machines and automation.
- Channel Partners. We are productizing the Faction platform and tools so that system integrators, IT and Cybersecurity services firms and Value Added Resellers of all types can offer, deploy, configure and manage Faction networks and data encryption for their customers and clients.
- Software Application Developers. When our APIs are ready, Faction networks can be easily integrated inside of applications and servers to secure your Web network infrastructure – and all the data it transports and stores – for staff, customers and users.
Virtual Private Circuits will be configured, deployed and supported by Faction VARs. We already have a few in place and will continue to expand in this area. Please contact us for a consultation.
OEM Firmware Integration and Customization Options #
Manufacturing
Cameras
Green Tech
Healthcare
Robotics
Drones
Integrate our firmware into your router, modem or smart devices and products or request customization for your the system and devices you wish to protect.
Faction Networks #
- Fully Decentralized, Unhackable in the CloudThe Faction Owner – and NOBODY else – creates and controls keys that encrypt both the network and data
- Unspoofable, UnphishableAuthentication is accomplished in a completely out-of-band method. Zero exposure to Cloud hacks.
- Networks Are Invisible and Connections Secure by DefaultFACTION PROTOCOL: It is impossible to see or connect to a Faction Network until invited and authenticated by the Faction owner.
- Data is Always EncryptedData is encrypted wherever it goes, and can only be decrypted on endpoint devices by Faction Members. Keys are never stored in or accessible to the Cloud
Take Your Critical Devices OFF the Internet #
Faction Pod for the Smart Manufacturing, Office and Remote Work #
Faction Pods change the game to easily and flexibly secure all of your smart, dumb and legacy devices in the networked distributed workplace, smart manufacturing and Infrastructure.
- Protect Your CamerasCamera’s pervade and watch every aspect and minute of our lives today. While we use, enjoy and rely upon them, none of them are secure or private.
The Faction Pod enables you to take control of who and what can connect to your camera, and where the data goes. - Protect Your Smart and Dumb DevicesThe Faction Pod enables you for the first time to protect:
- Smart Home & Office Devicesnetwork attached storage drives, printers and other office appliancesLocal Data Servers
- Access and Share Them on Your Personal Private NetworkEach Pod is a local gateway to your Faction PPN, so you can:
- securely share these devices across any number of locations – local or global
- and exit from each location for Private Web browsing too!
Data Encryption #
Faction Your Email, Cloud Drives & File Sharing #
Thanks to your Faction PPN, we can securely distribute and manage unbreakable AES 256 symmetric encryption keys controlled by YOU to protect your data wherever it goes.
- Faction Your EmailUse your favorite email application, but encrypt the contents of your messages with your personal X.509 certificate signed with your own private key
- Faction Your Cloud DriveEncrypt all the folders & files with private keys that only you and your Faction Members possess to decrypt them.
- Faction Network Drive & File SharingShare and back-up files with your own distributed network of drives and devices .with ZERO Cloud exposure
Join our Pilot Program to Try Faction Now #
We are now accepting pilot customers and partners into our program. If you are interested, please fill out the form below to apply, and we will be in touch very soon!