Faction Virtual Private Circuits provide a unique solution to protect critical but vulnerable smart, dumb and legacy devices that populate our lives, workplaces, homes – and even our bodies. While every industry has many of these, we are focused in particular on these 3 verticals
Manufacturing #
Healthcare #
Green Energy #
What We Are Doing is Not Working #
The headlines and statistic get grimmer year after year. With hostile state actors now actively collaborating with criminal gangs, and cyberwarfare the new normal, the status quo is not sustainable
Remember the T1? We do. #
There was a day when no organization would have ever considered connecting mission critical devices – such as smart manufacturing machinery, home and personal healthcare devices, charging stations and other decentralized infrastructure – directly to the Internet. It is simply too risky.
For 30 years, organizations leased T-1 lines, a secure but costly way to have a totally private network to connect critical machines and devices and the computers and servers that are needed to monitor and control them. But then, something happened: T-1 lines were phased out! One by one, these internal networks were moved onto the Internet and securing these connections become the job of VPNs, Firewalls and SDNs.
Unfortunately, the Internet is fundamentally compromised and more organizations are discovering every day that these tools simply cannot secure mission critical machines and devices.
That’s Why We Created the Faction Virtual Private Circuit #
The Faction Virtual Private Circuit (VPC) is a Business VPN replacement for small to midsized organizations or collaborative teams that need to secure distributed workplaces with lots of smart, dumb and legacy devices. VPCs:
- Eliminate the vulnerabilities of VPNs
- Avoid the pain, complexity and costs of SDNs/ZTNA
- Help protect your organization – and customers / users – from catastrophic attack
It’s a Simple but Powerful Idea #
Get your critical users, devices and systems – including cloud servers – OFF of the Internet and into your secure, private Faction Virtual Private Circuit.
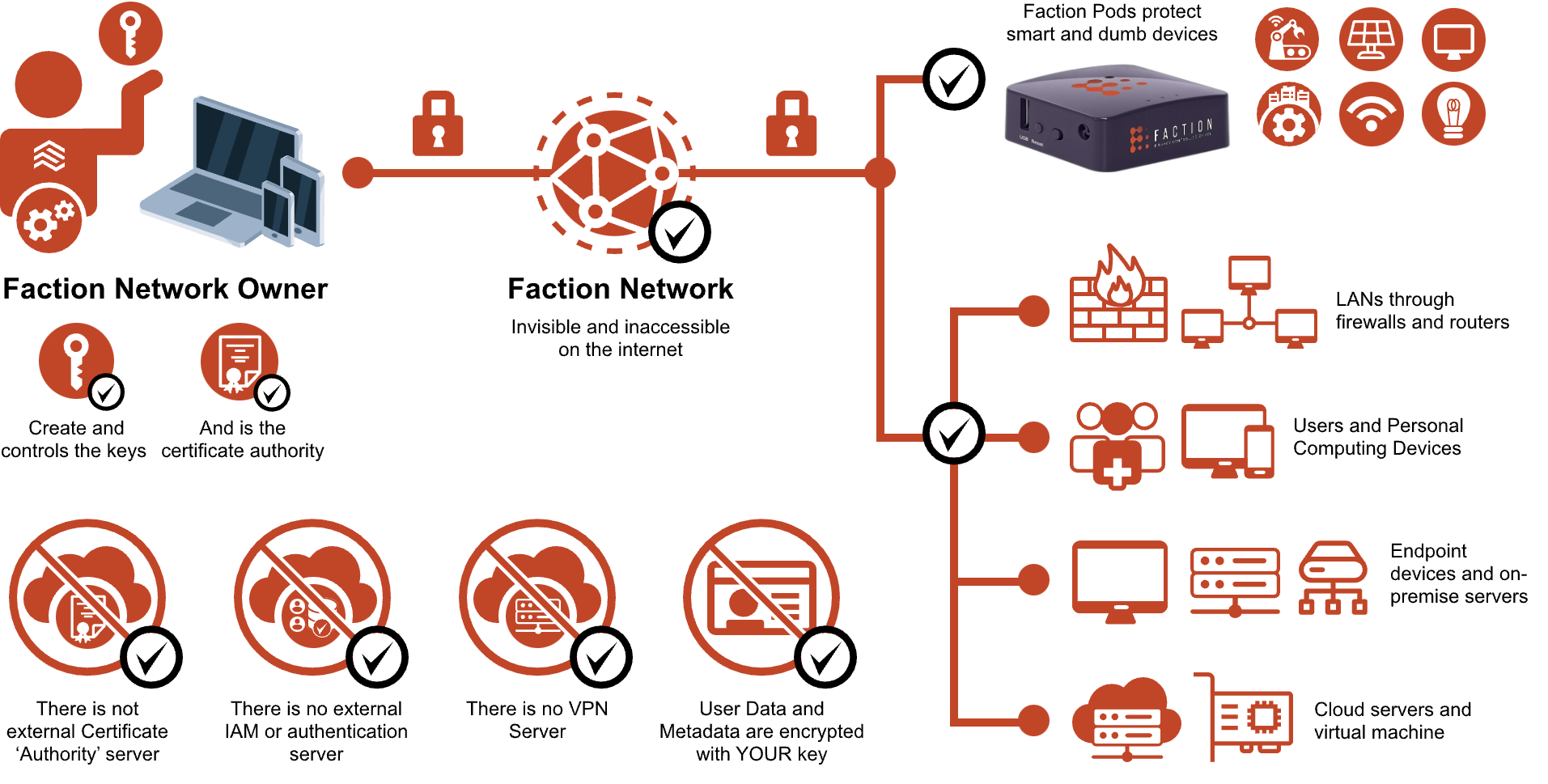
Faction is Low Cost and Easy to Deploy and Use #
The even better news is that Faction Networks are far less expensive, far more flexible and far easier to manage than a T1 – or all the expensive hardware and software that is thrown at the unsolvable problem of keeping devices which are connected to the Internet safe!
- Uncompromising Security: Faction Networks and Pods provide unparalleled protection against cyberattacks, safeguarding your data and privacy from even the most sophisticated Internet-based attackers.
- Peace of Mind: Enjoy the freedom of knowing your network and critical devices are invisible and your information is safe.
- Simple Installation: The Faction Pod is plug-and-play, making it easy to set up and enjoy immediate protection.
- Seamless Integration: Works seamlessly with your existing Internet infrastructure and all of our devices – computers, tablets, smartphones, smart office devices, dumb devices, legacy machines on the production line, you name it – requiring no additional configuration.
- Affordable: Get industry-leading protection at a cost that fits your budget.
Faction Also Protects Your Data #
While devices are critical, data can often be an even more valuable target. When we think of data, the focus tends to be on ‘SaaS (Software-as-as-Service) cloud applications. While businesses have made strides in recent years to improve security of authentication with 2FA and authenticator apps, most have entirely forgotten about all the data lying around on endpoint devices like computers, tablets, smartphones and cloud drives. In fact, businesses protect just 3% of folders online (and 88% of businesses have 1+ million folders). When ransomware attack occur, this is usually the data that is encrypted and held hostage!
If You Want Data to Be Secure, You Must Encrypt at All Times
Everybody knows this, but almost nobody does it – except in narrow use cases or complex and expensive Enterprise solutions requiring support from IT. Why? But Its Too Damn Hard! Here’s the problem:
- Data encryption platforms and methods used today are complex and have poor UX.
- So people don’t use encryption widely or systematically to protect their data.
- So the hackers and ransomware gangs win.
Faction Makes It Easy
Faction eliminates the pain points of encryption for end users, developers and IT staff, so it can be USED widely and systematically to protect data both in transit and at rest on devices, the cloud and even in 3rd party applications.
THE SOLUTION #
Faction Puts You In Control #
Your Keys. Your Network. Your Data.
Thanks to multiple groundbreaking innovations, Faction combines capabilities simplifies, streamlines and eliminates many of the paint points of Virtual Private Networks, Software Defined Networks and Data Encryption. The result of all this is a solution that enables everyday users, small to mid-sized businesses and distributed teams to take control of their own security for their most important communications, devices and data.
Networking
Create and Control Your Own Personal Private Network
Endpoint-to-Endpoint
The Cloud is Compromised – so remove it from the equation
Easy to Use
Encrypt data at ALL times with keys created and controlled by the data owner
Devices
Take smart, dumb and legacy devices that cannot protect themselves OFF of the Internet into your Faction Network
Data
Encrypt data at ALL time with keys created and controlled by the data owner
Join our Pilot Program to Try Faction Now #
We are now accepting pilot customers and partners into our program. If you are interested, please fill out the form below to apply, and we will be in touch very soon!